I’m worried about the security of my SFTP setup after noticing some suspicious login attempts in my server logs. I’m unsure if my configuration is strong enough to protect sensitive data. Can anyone suggest the best practices or additional security measures I should implement?
Here’s My Take on SFTP Security and Mounting Drives (Not a Pro, Just an Experienced User)
Let me preface by saying I’m not a cybersecurity guru—just someone who’s wrestled with more file transfers than I care to count. SFTP (Secure File Transfer Protocol) is what you get when your files start wearing armor: it’s built on SSH, meaning your data doesn’t travel through the digital wild west naked. Instead, everything’s encoded in such a way that nosey interlopers can’t peek or fiddle with it. So yeah, if your paranoia levels are justifiably high when moving sensitive documents, SFTP has your back.
Now, it’s not just about wrapping data in digital bubble wrap. SFTP asks you, “Who goes there?” via passwords or SSH keys before letting you through the gate. I can’t count the times having a robust authentication system saved my bacon, even when I was an “oops, copy-paste password” type of user.
The Grind: Mounting SFTP Servers on Windows Without Pulling Your Hair Out
So, if your job (or side hustle, or weird hobby) brings you face-to-face with SFTP servers—especially on Windows—boy, do I relate. My workflow got tired of endless window switching and the whole juggling act, so I ended up relying on CloudMounter to tie everything together. Not a paid endorsement, just what got me out of digital chaos.
Step-by-Step: SFTP as a “Just Another Drive” Setup
-
First hurdle: Download and install CloudMounter. If you can install a game, you can install this.
-
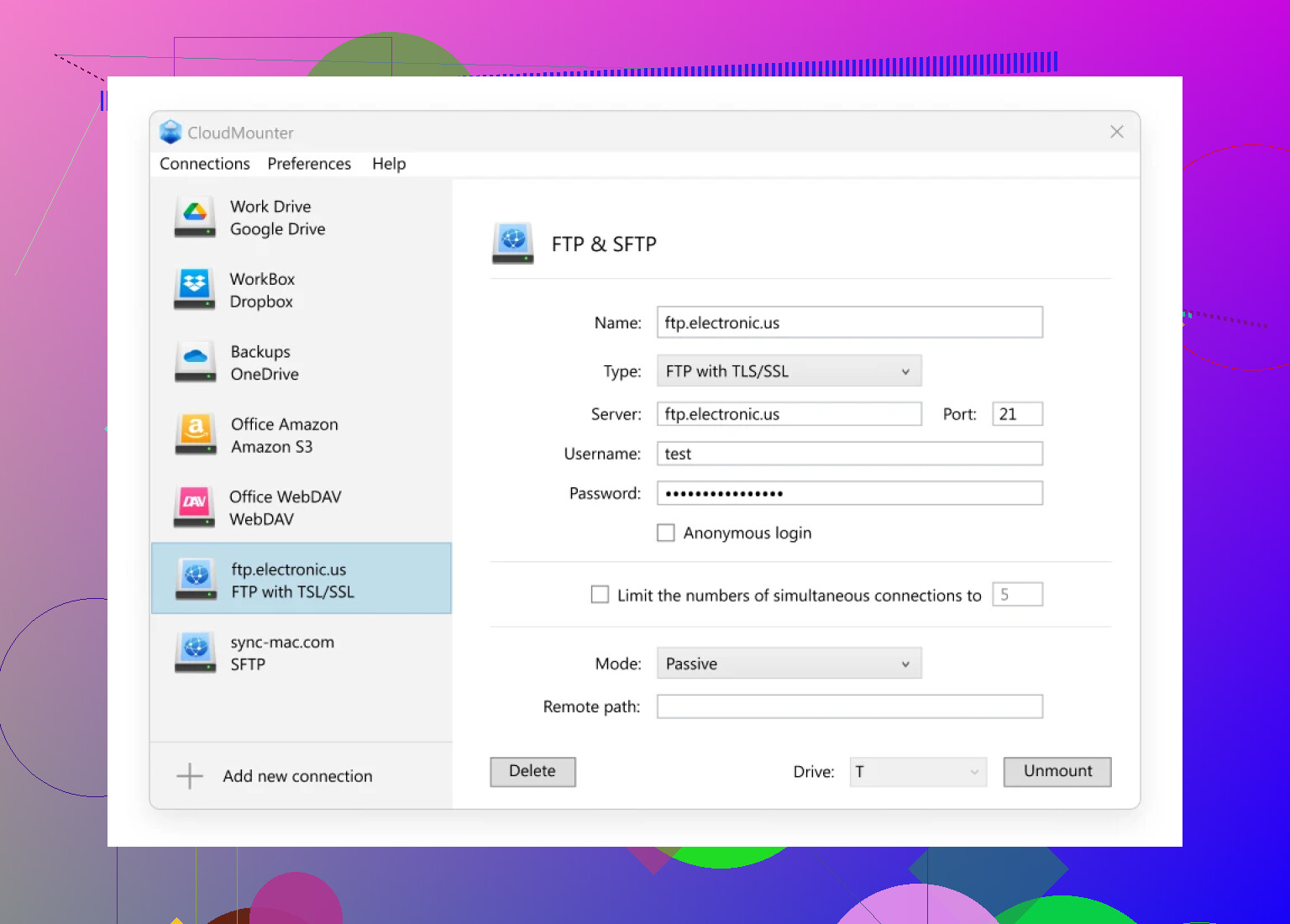
Opening moves: Fire up the app. Instead of drowning in connection jargon, just tap the “FTP & SFTP” option—you really can’t miss it.
-
Fill in the blanks: Choose SFTP, punch in your connection info (hostname, username, the whole nine yards), and whack that “Mount” button like you mean it.
-
Here’s what you’ll see:
-
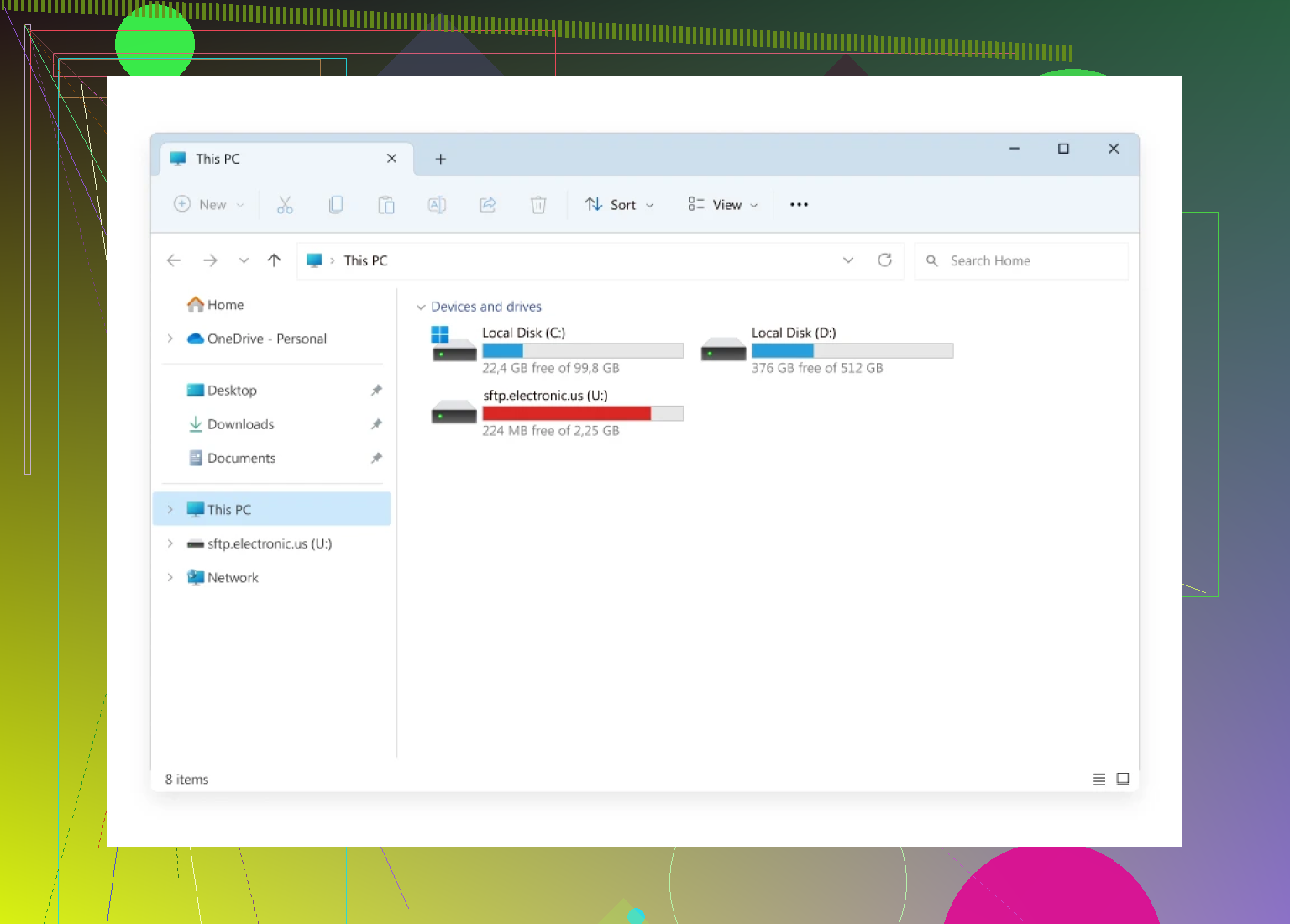
Voilà: Head over to File Explorer and, like magic, there’s your SFTP server chillin’ as if it were any other drive plugged into your tower.
If you’re someone who’d rather not juggle a dozen finicky apps or browser tabs just to fetch files from “that one server,” this setup keeps things civilized. No more copy-paste mishaps or files lost to the ether. Just point, click, and your distant server feels like it’s right at home on your desktop.
That’s about the gist. You don’t have to trade sanity for security—tools exist, and hey, sometimes they actually work.
Oof, those suspicious login attempts are the digital version of hearing creaks on your staircase at 3am. @mikeappsreviewer covered a lot on mounting SFTP in Windows—dig that, but let’s crank up the actual security side of things. Here’s my straight-shooter take, skipping the Windows mount magic for a sec (even though CloudMounter’s cool for ease).
- Kill password logins if you can. SSH key auth only, period. Passwords are always the weak link, even if “Hunter2!” was a stroke of genius in 2007.
- Move SSH off port 22. It’s not bulletproof, but with 2.5 million bots set on sniffing port 22, you’ll drop the script kiddie noise by a mile.
- Use fail2ban or similar. If someone’s hammering login attempts, auto-ban their IP. Log in, fail thrice, you’re iced out for a week.
- Whitelist IPs. If you know where you’re connecting from (home, office), set the firewall so only those IPs can hit the SFTP port.
- Audit user privileges. No “one account does all.” Give each user only what they need, chroot ‘em into their home if possible.
- Regularly update. No config fix undoes unpatched vulnerabilities. If you’ve ignored that blinking “update available” for OpenSSH… don’t.
- Watch them logs. Not just for failed logins, but weird SFTP commands, new users, etc. Set up alerts so you don’t have to check manually.
- Consider 2FA for SSH. A bit overkill for some, but if the data’s nuclear-grade, look into Google Authenticator or similar PAM modules.
Mounting tools like CloudMounter are a workflow blessing (serious, the alt-tab hell is real), but none of those windows matter if you leave the server wide open. Don’t be that guy who double-locks his front door but leaves the attic window wide open.
TL;DR: Ditch passwords, ban quickly, lock down access, keep stuff updated, and treat suspicious logs like a kitchen fire.
Here we go, the eternal “let’s make SFTP bulletproof” thread… I see @mikeappsreviewer and @sterrenkijker covered CloudMounter for Windows workflow and hit most of the usual SSH lockdowns (props on chroot & kill password logins). But let’s be honest, you can pile up all these best practices and still trip if you overlook some less-popular but REAL security holes.
First, if you’re seeing suspect login attempts, your server’s on the radar. Don’t just kneejerk and change the SSH port—bots find random higher ports too, just takes longer. Port knocking is a pain but actually shields your port until you “knock” with the right sequence. Not a daily driver fix, but not as breakable as “just use port 2222.”
Also, multi-factor auth is cool, but let’s be realistic—it’s overkill if you’re trading cat pics. But if anything even remotely sensitive’s up there, DO IT. I personally use hardware keys (Yubikey)—WAY less hackable than phone-based OTP apps, if you’re serious.
Please, don’t think fail2ban is perfect—if someone is rotating through VPNs or using a botnet, you’ll just see endless new attempts. Network-level protections (e.g., using a VPN so your SFTP is only accessible from VPN-internal IPs) are a much bigger headache for attackers. It’s not the easiest thing to set up, but it’s the kind of paranoia that actually pays off.
Audit your SSH config. Do you REALLY need root login? Disable it. Are you using GSSAPI, Kerberos, ancient ciphers? Switch them off. Your /etc/ssh/sshd_config file should be boring, minimal, and commented within an inch of its life.
Pro-tip nobody talks about: Run SSH on a separate, unprivileged user with its own strict limits, not just your regular system account. Sandbox if possible. It’s less convenient but can limit the damage if one account gets popped.
If you’re transferring files back and forth all the time, and want a mapped drive, CloudMounter is fine, but do NOT let these mount-anything-anywhere tools hold on to your private SSH keys with no passphrase. Some more user-friendly programs load everything into RAM and don’t always manage it safely. If you must, use agents with timeouts.
Finally, about monitoring—log files are cool, but real security comes from alerts. Spin up a SIEM, even a low-budget one, and actually forward logs OFF the server. More than one admin’s been burnt because attackers just nuked the evidence.
Sure, @mikeappsreviewer made mapping SFTP on Windows idiot-proof, and @sterrenkijker’s run down is solid. But SFTP threats evolve. Anything public-facing is a ticking timebomb of bot-sweat and zero-days. Lock it, log it, and assume tomorrow’s attack is already smarter than your config last week.
Three words: defense in depth. Oh, and don’t assume your SFTP “armor” is invincible just because you ticked the first five boxes on a 101 list.